Technology Forensics
OBJECTIVES:
1. Articulate the complexities of network and application infrastructure and apply critical thinking skills to how they affect technology forensics investigations and incident response procedures
2. Identify and apply in a forensics context the various topologies, standards,
technologies and protocols employed in computer systems, including file system formats and their attributes.
3. Evaluate, select and deploy computer forensic measures for the response,
mitigation and analysis of a security incident pertaining to digital artifacts and how information was compromised.
4. Analyze and evaluate the current investigative and legal aspects of information and computer forensics, including electronic discovery, depositions, litigation and corporate personnel processes.
5. Evaluate and execute the strategies, methodologies, techniques and state-of-the-art forensics tools for the preservation of digital evidence on computer systems, network systems and other electronic devices.
6. Create tracking processes to follow the trail of electronic evidence through digital systems, including documentation, formal reporting and presentation
01
Objective One: Articulate the complexities of network and application infrastructure and apply critical thinking skills to how they affect technology forensics investigations and incident response procedures
Project: Malware – CFR101
In this lab, you will be using a computer in the cluster in the SOC to analyze actively working malware in a controlled environment. Then, taking what you have learned, write a report on the piece of malware you picked. This hands-on experience will provide you with valuable insights into the behavior and characteristics of different types of malware, enhancing your ability to detect and respond to threats effectively. Additionally, writing a detailed report will help you solidify your understanding of the malware's impact and potential mitigation strategies.
This document meticulously analyzes the infection of a windows operating system. The document defines the applications infrastructure and the suspicious processes observed on the operating system. The technical analysis applies critical thinking to the persistence and defense evasion mechanisms at play.
01
Final Project – NTS103
Determine what personal information can be found related to you.
Explain the threats to your personal information and identity.
Apply methodologies and strategies for protecting your personal information and identity.
Describe concepts of physical security protection and develop strategies for your self-protection.
Analyze publicized identity theft incidents.
Identify and assess the risks associated with social media.
Understand the concepts of physical security protection and develop strategies for your self-protection
This document is a personal risk assessment. The assessment applies critical thinking to security vulnerabilities in my current life and brainstorms solutions to each vulnerability.
Objective One: Articulate the complexities of network and application infrastructure and apply critical thinking skills to how they affect technology forensics investigations and incident response procedures
Objective 2: Identify and apply in a forensics context the various topologies, standards, technologies and protocols employed in computer systems, including file system formats and their attributes.
02
Assignment: OS Forensics Follow-Up Questions – CFR101
Name two persistence mechanisms that do not require the use of the registry.
What files can be obtained by parsing the contents of a prefetch folder?
Name two persistence mechanisms that an attacker can use to maintain access to a compromised Mac?
What is "journaling" in the Mac OS system?
This document details the persistence mechanisms, technologies and processes used by malicious actors to maintain access to a compromised Mac computer.
02
Assignment 3.1: Simulating Allocation and Access – CFR105
The goal is to inspect a file’s metadata using system calls or command-line tools.
This document describes the process of inspecting metadata using Linux CLI. The document observes the File name, byte size, byte blocks, IO blocks, device ID, inode number, and hard links.
Objective 2: Identify and apply in a forensics context the various topologies, standards, technologies and protocols employed in computer systems, including file system formats and their attributes.
Objective Three: Evaluate, select and deploy computer forensic measures for the response, mitigation and analysis of a security incident pertaining to digital artifacts and how information was compromised.
03
Project: Malware – CFR101
In this lab, you will be using a computer in the cluster in the SOC to analyze actively working malware in a controlled environment. Then, taking what you have learned, write a report on the piece of malware you picked. This hands-on experience will provide you with valuable insights into the behavior and characteristics of different types of malware, enhancing your ability to detect and respond to threats effectively. Additionally, writing a detailed report will help you solidify your understanding of the malware's impact and potential mitigation strategies.
This project has Mimikatz as the selected malware and analyzes the artifacts left by it to create a mitigation plan and recommendations to secure the computer.
03
Assignment: Hard Drive and Tools Follow-Up Questions – CFR101
Objective Three: Evaluate, select and deploy computer forensic measures for the response, mitigation and analysis of a security incident pertaining to digital artifacts and how information was compromised.
Describe the steps and considerations you would use to create the standard hard drive imaging process for an organization.
Describe what you would do to validate a new forensic tool on the market you are looking to buy.
How could you quickly identify whether a large pcap file with thousands of session contained FTP traffic?
Are network services critical to Incident Response? If DHCP logs are not available how would you determine what system an IP belonged to?
Name some common ways you might discover services or applications that are helpful to an investigation.
This document covers the steps and considerations forensics professionals would use to create a hard drive image and analyzes different processes to discover services helpful to the investigation.
04
Objective Four: Analyze and evaluate the current investigative and legal aspects of information and computer forensics, including electronic discovery, depositions, litigation and corporate personnel processes.
Assignment: Current Computer Forensics Case – CFR101
you are tasked with researching a recent case that has been covered in the media where computer forensics could have played a crucial role. Your objective is to provide a comprehensive understanding of the pitfalls and obstacles faced by the examiner involved in that specific case.
This document covers the 2023 Real Estate Wealth Network data breach and analyzes the incident response teams processes and procedures. The documents cover what was available to the incident response team and how they secured sensitive information.
04
Assignment 2.2: Case Project 2: Distributed Denial-of-Service (DDoS) Attacks – NTS201
Discuss the organizational need for information security
Explain why a successful information security program is the shared responsibility of an organization’s three communities of interest
List and describe the threats posed to information security and common attacks associated with those threats
List the common development failures and errors that result from poor software security efforts
This document analyzes Direct Denial of Service attacks and describes the processes and procedures of controlling the severity of a DDoS attack through litigation of roles, strengthening of tools, and monitoring of services.
Objective Four: Analyze and evaluate the current investigative and legal aspects of information and computer forensics, including electronic discovery, depositions, litigation and corporate personnel processes.
Objective Five: Evaluate and execute the strategies, methodologies, techniques and state-of-the-art forensics tools for the preservation of digital evidence on computer systems, network systems and other electronic devices.
05
Final Practical Exam – CFR101
Your job will be to create copies of all the evidence
Show HASH for files to prove no tamping of evidence
Then, search all the files and document any relevant evidence you find
Find out who was involved and make a list of evidence that ties them to the case
Also, make sure we aren’t holding anyone we don’t need to.
find Motive and how this crime was accomplished
This document follows the steps and procedures of a tech forensics analyst. The document includes the name of evidence owner, description of evidence, hash of file, location of file, date of discovery, and encryption of file.
05
Assignment: Memory and Volatile Data Analysis – CFR101
Objective Five: Evaluate and execute the strategies, methodologies, techniques and state-of-the-art forensics tools for the preservation of digital evidence on computer systems, network systems and other electronic devices.
Define computer forensics and how to apply its concepts; including how to prepare for a computer investigation and the requirements for computer forensics labs.
Demonstrate the different ways for sound data acquisition, including proper handling and acquisition of digital Able to determine how data is stored and managed by the operating system.
Use computer forensic tools to reconstruct graphics files, analyze networks and email, identify and locate malware/viruses, and validate evidence for forensic reports.
Testify in a courtroom setting as well as preparation for court and evidence presentation; including maintaining a high level of ethics.
This document outlines the process of using volatility workbench to collect system process information. Volatility workbench collects the PID, PPID,
ImageFileName, Offset, Threads, Handles, SessionID, Wow64, CreateTime, and ExitTime. All collected information was preserved on the document through screenshots.
06
Objective Six: Create tracking processes to follow the trail of electronic evidence through digital systems, including documentation, formal reporting and presentation
Project: Autopsy CTF1 – CFR101
Describe the fundamentals of a forensic investigation and explain how to preserve the chain of custody
Describe the common methods to extract information
Identify common tools and activities that are part of a forensic investigation
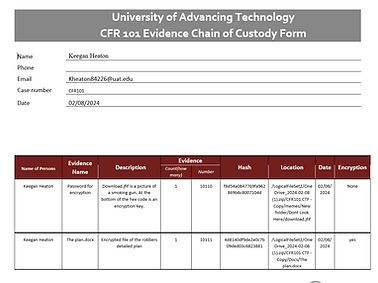
This document is a chain of custody form to preserve information related to changes made on the investigation evidence. The chain of custody form includes the name of examiner, name of evidence, description of evidence, evidence number, hash of file, location of file, date evidence was accessed, and encryption.
06
CTF2 Autopsy- CFR101
Define computer forensics and how to apply its concepts; including how to prepare for a computer investigation and the requirements for computer forensics labs.
Demonstrate the different ways for sound data acquisition, including proper handling and acquisition of digital Able to determine how data is stored and managed by the operating system.
Use computer forensic tools to reconstruct graphics files, analyze networks and email, identify and locate malware/viruses, and validate evidence for forensic reports.
Testify in a courtroom setting as well as preparation for court and evidence presentation; including maintaining a high level of ethics.
This document is written in a standardized professional format. The document covers the timestamps and actions taken while performing a forensic investigation on a windows operating system image. The document contains the file name, access date, Autopsy version, statement of intention, and description of discoveries.
Objective Six: Create tracking processes to follow the trail of electronic evidence through digital systems, including documentation, formal reporting and presentation